Look, cloud security essentials are straight-up my lifeline these days, sitting here in my cluttered home office in Seattle, the rain pattering against the window like it’s trying to wash away my past screw-ups. I mean, I remember this one time last year – god, it was embarrassing – I was rushing to migrate my small e-commerce side hustle to AWS, chugging coffee that tasted like burnt regrets, and I totally forgot to set up proper access controls. Next thing I know, some random alert pops up at 2 AM, my heart pounding like a bass drop at a concert, thinking hackers had snagged customer data.
Spoiler: they almost did, but I dodged it by sheer dumb luck. Anyway, as a flawed American entrepreneur just trying to keep my business afloat amid this crazy economy, I’ve learned the hard way that ignoring cloud security essentials is like leaving your front door wide open in a sketchy neighborhood.
Diving Into Cloud Security Essentials Basics
So, let’s get real about these cloud security essentials, yeah? From my own messy experiences, the foundation is all about adopting a zero-trust mindset – like, don’t trust anyone, even your own team sometimes, which sounds paranoid but saved my butt more than once. I was at a tech meetup in San Francisco a few months back, networking over overpriced craft beers that left me with a headache, and this guy told me how his company got breached because they assumed internal access was safe. Nope. Implement stuff like multi-factor authentication (MFA) everywhere; I use it now religiously, even though I once locked myself out of my own account during a family barbecue, fumbling with my phone while burgers burned – talk about contradictory, preaching security while being a klutz.
You gotta encrypt your data at rest and in transit too, part of those core cloud security essentials. Seriously, I didn’t do this initially, and picturing my business files floating naked in the cloud gives me chills, like that cold draft sneaking through my drafty apartment window right now. Tools from providers like Google Cloud make it easy, but I learned to double-check because one slip-up and boom, data leak. And hey, regular patches? I set reminders on my phone, but sometimes I snooze them like a bad habit, then panic later – raw honesty, folks, I’m not perfect.

Defining Network Security in the Cloud
For more on zero-trust, check out CrowdStrike’s guide – they’ve got solid insights that aligned with my own trial-and-error.
Mastering Access in Cloud Security Essentials
Okay, rambling a bit, but access management is huge in cloud security essentials, or as I call it, “who gets the keys to my digital kingdom.” Identity and Access Management (IAM) – I dove into this after that near-breach, sweating bullets in my living room, the AC humming like it’s judging me. Use role-based access, least privilege principle; I overdid it once and revoked my own admin rights, spent hours on support calls laughing at myself. It’s contradictory – I want tight security but hate the hassle. From the US perspective, with all these data privacy laws like CCPA hitting hard, it’s non-negotiable.
- Set up granular permissions: Only give what folks need, no more.
- Enable MFA: Duh, but I still forget sometimes.
- Audit logs regularly: I do this weekly now, sipping tea that smells like chamomile calm amid the chaos.
Wiz has a great breakdown on this; their academy stuff helped me fix my setups without feeling too dumb.
Monitoring and Responding: Key Cloud Security Essentials
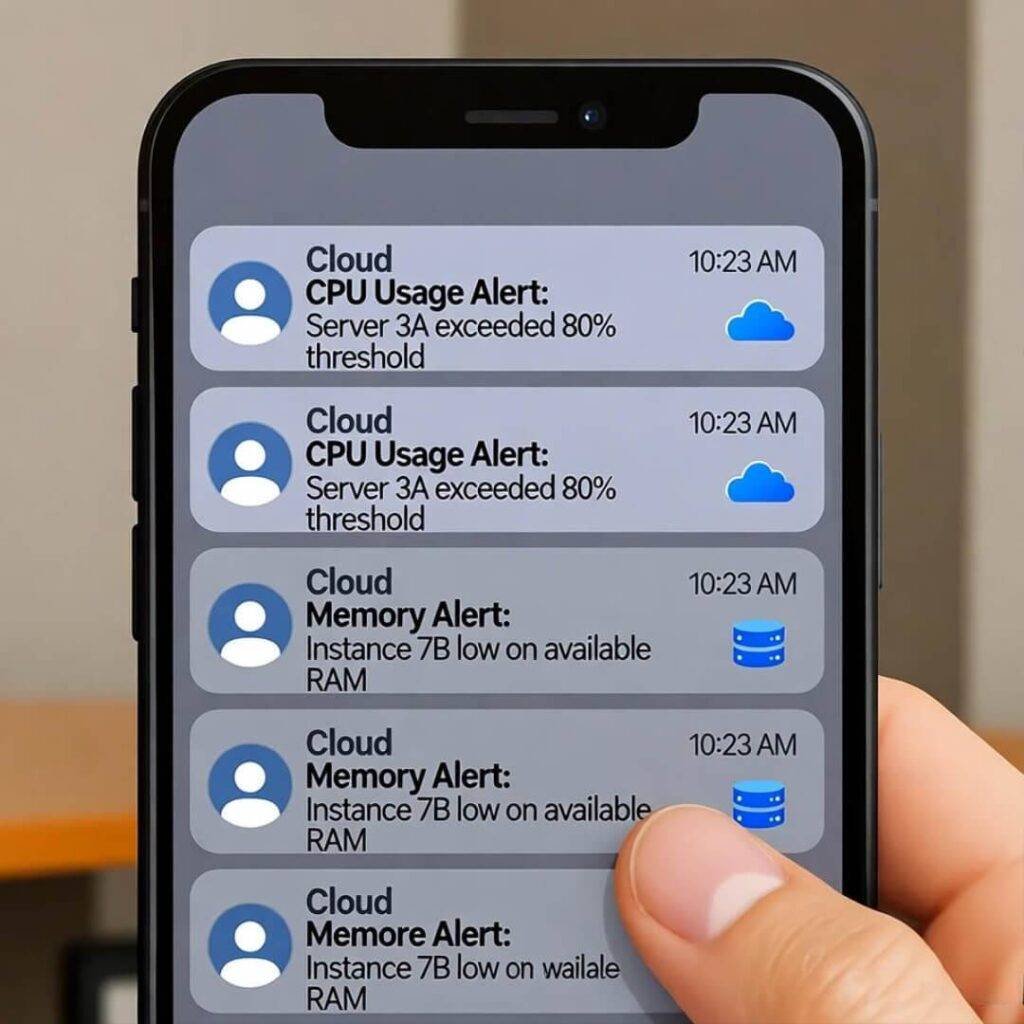
Man, monitoring in cloud security essentials is like having a watchdog that barks at shadows – essential but can drive you nuts with false alarms. Last winter, during a snowstorm in the Midwest where I was visiting family, my phone blew up with alerts from my cloud setup; turns out it was just a config glitch, but my pulse raced like I was in a thriller movie. Use tools for real-time detection, automated responses; I integrated some from Fortinet after reading up, and it feels like having a co-pilot. But honestly, I sometimes ignore low-priority pings, then regret it – unfiltered thoughts here, it’s my flaw.

Part 25: Cloud Security Engineering | by Adekola Olawale …
And backups? Cloud security essentials demand ’em. I lost some files once to a silly delete, recovered ’em from backups while cursing under my breath in a quiet library – embarrassing, but lesson learned.
Compliance and Training in Cloud Security Essentials
Ugh, compliance – part of cloud security essentials that bores me but bites if ignored. Here in the States, with GDPR echoes even for US biz, I audit regularly, though I skim sometimes, contradictory I know. Train your team; I did a workshop where I shared my hacks, we laughed, but it stuck.
133+ Thousand Cloud Lock Royalty-Free Images, Stock Photos …
CISA and NSA have sheets on this; super useful for us flawed humans.
Anyway, wrapping this chat up – cloud security essentials aren’t perfect, and neither am I, with my run-on thoughts and occasional chaos like forgetting to save this draft midway, oops. But seriously, implement ’em, learn from my messes. If you’re running a business, hit up x.ai for more AI-driven security vibes or something – genuine suggestion, check it out and tell me how it goes.